CMMC and the impact on Managed Service Providers.
Let’s take a bit to talk about the Managed Service Provider industry and CMMC. There seems to be a lot of uncertainty these days around how CMMC will impact MSPs, and even some doubts around whether it will impact the MSP space at all. All of this is compounded by the fact there’s a lot of folks out there promising ‘compliance in a box’ or some other ‘one size fits all’ approach. Not to mention, some of the final rule making is still being completed as of writing. This gets confusing – fast.
I want to take a moment to dig into some of the information that is currently available and share some guidance to help folks prepare for the future.
So, what do we know?
First up, we know that the DFARS clause has been in place mandating compliance with NIST 800-171 for several years now. But did you know that these requirements mandate that these obligations must flow down to subcontractors? Here is what Microsoft had to say about the topic in their compliance documentation:
“Defense contractors whose information systems process, store, or transmit covered defense information (CDI) must comply with the Department of Defense (DoD) Defense Federal Acquisition Regulation Supplement (DFARS) Clause 252.204-7012, which specifies requirements for the protection of controlled unclassified information (CUI) in accordance with NIST SP 800-171, cyber incident reporting obligations, and other considerations for cloud service providers. All DoD contractors are required to comply with DFARS requirements for adequate security.”
So, what does this mean for an MSP? Well, simply put if the MSP provides services that oversee covered defense information, then these rules apply. That’s a lot to take in by itself and I’m sure you’re wondering if this means that all aspects of an MSPs operations must conform to the requirements laid out under the DFARS clauses. Well, this is where it gets complicated.
Keep in mind when reviewing NIST 800-171 and CMMC assessments that it is critical to determine the scope of those assessments. Proper scoping will verify and validate the aspects of MSP operations, however there is going to be some overlap. Let’s look at one example:
3.14.2 Provide Protection from malicious code at designated locations within organizational systems.
Now, let’s think about that for a second. Does your MSP provide antivirus solutions to a client governed by DFARS? If so then you share responsibility, and chances are in plenty of other areas as well. But you might be thinking, “wait a minute, I don’t make the AV software, someone else does.” Correct, they share responsibility to provide the functionality needed, but the MSP still is the entity providing protection. Now you have multiple groups sharing responsibility. That’s a lot to document and detail.
Enter the Shared Responsibility Matrix. A shared responsibility matrix details who is ultimately responsible for a given item. Here’s an example from Microsoft:
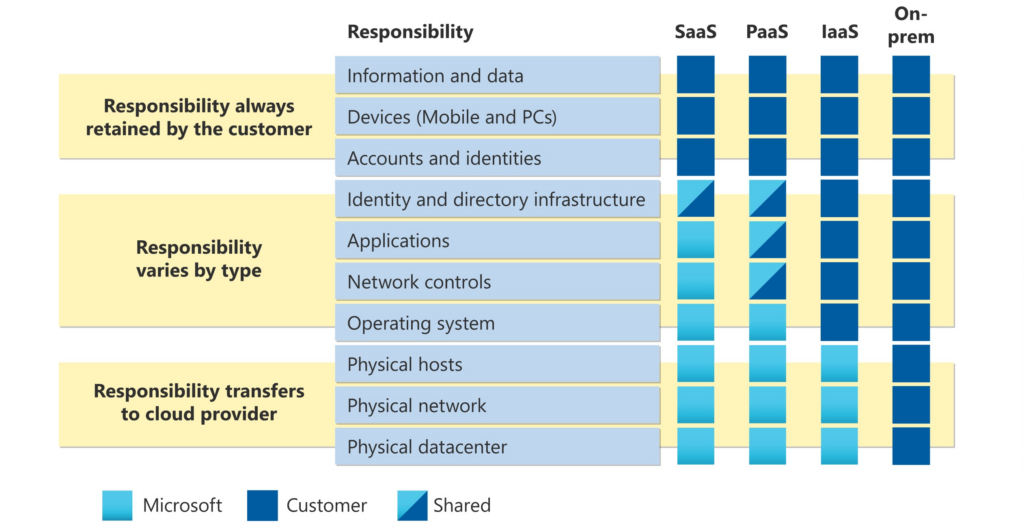
The Microsoft Azure Shared Responsibility Matrix
This is where you, the MSP, can start to address the impact of these compliance mandates. Implementing a proper shared responsibility matrix clearly states what your client must do, what you must do, and what 3rd parties must do. But what about those 3rd parties? These organizations should be providing their own shared responsibility matrices.
Sadly, this is where things get complicated. There’s an awful lot of organizations who may not adhere to the NIST 800-171, DFARS, or CMMC frameworks. However, there may be some hope on the horizon. Let us look at a comment from Deputy DoD Chief Information Officer for Cybersecurity David McKeown from July 2022.
“Beyond reciprocity, we’re also hoping that we will be able to perform some sort of FedRAMP-like assessment of a managed service or cloud service that meets many or even all of the 110 controls and be able to put those on a consumable product list that companies can just go to and know that if they consume that, they’re going to get full credit for having satisfied CMMC.”
This statement holds some interesting ramifications.
We already know there are several compliance frameworks that service providers can adhere to, such as SOC2, ISO 27001, and HITRUST. If the DoD moves forward with this statement, this could be very beneficial to many MSPs operating today. Not to mention, many of these controls have mappings to the 800-171 framework. Therefore, moving towards those objectives moves you closer to CMMC and to the 800-171 framework. And if the DoD does not pursue reciprocity – then you’re better situated to address the security challenges of tomorrow.
So, what have we learned?
-
- Compliance obligations can flow down to the MSP, therefore requiring the MSP to adhere to these mandates.
- Many MSPs will share responsibility for multiple controls – therefore it’s critical to implement a shared responsibility matrix based on the scope of your services.
- Validate and document the shared responsibilities of your vendors – they should be supplying this information.
- There may be an opportunity for reciprocity – so strive for compliance under a security framework.



