Some Uncomfortable Truths About “Compliance Automation”
Everyone wants automation.
Managed Service Providers (MSPs) want it to scale faster.
Clients ask for it because they assume it means efficiency.
And vendors promise it because it sells.
But here’s the uncomfortable truth: you can’t automate your way to real compliance. Automation supports compliance, but it doesn’t replace it. Without governance, automation is just data without direction.
This is the core challenge of compliance automation; tools can streamline tasks, but they can’t replace accountability.
“Automation without governance is just data and data doesn’t prove compliance.”
Pulling configurations through APIs or flagging insecure settings looks impressive on a dashboard. It’s efficient, yes, but it isn’t enough. Real compliance is about proof, not just performance. It’s about governance, not just data.
Automation can collect evidence, but it can’t explain why a control exists, who owns it, or how it’s maintained. Those are governance questions, and governance is still a human discipline.
The Human Layer of Compliance
Every major security and compliance framework; from the CIS Controls and NIST Cybersecurity Framework to SOC 2 and ISO 27001, depends on human oversight.
Automation can detect, compare, and record. But it cannot interpret risk, prioritize remediation, or validate that a process was followed correctly. That limitation is at the heart of compliance automation, where efficiency often outpaces context, and context comes from people who understand both the technical and business impact of each control.
That’s why the idea of fully automated compliance is incomplete. The tools may gather the data, but humans determine whether that data demonstrates governance. Without that interpretive layer, automation alone becomes noise fast, but not defensible.
Why Automation Doesn’t Equal Assurance
Across the MSP and cybersecurity landscape, the same question surfaces again and again:
“Can you automate that?”
It’s a fair question, but often the wrong one. True compliance automation isn’t about removing people from the process; it’s about giving them better visibility.
Most organizations want integrations that “just work.” They assume that if a compliance management tool can connect to their RMM or pull data from Microsoft 365, it’s equivalent to satisfying a control. But compliance isn’t just about confirming a setting; it’s about proving a process.
Turning on multifactor authentication isn’t the same as documenting an MFA policy. Exporting configurations from Intune doesn’t replace a formal Standard Operating Procedure (SOP). Governance still matters.
Automation without policy alignment leaves gaps, gaps that auditors, regulators, and insurers will eventually find.
What Compliance Automation Really Means for MSPs
That brings us to one of the biggest misconceptions we see among MSPs: Integration is not compliance.
Some vendors advertise that they integrate with AWS, Microsoft 365, or third-party security tools, as if those connections alone establish governance. But compliance automation that focuses only on integrations misses the governance layer entirely. In truth, data integration is only one component of a mature GRC program.
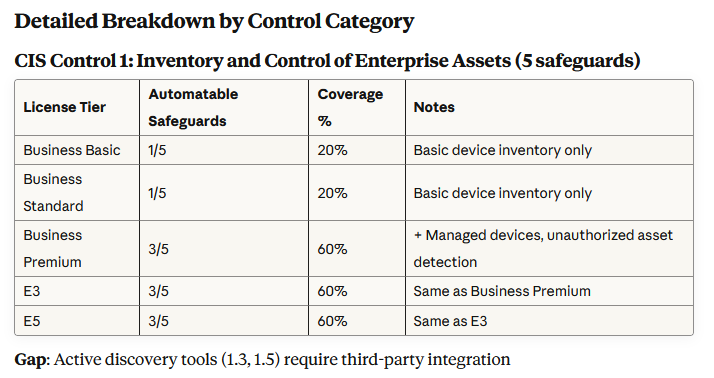
Consider CIS Control 1.1 – Enterprise Asset Management. Pulling device data from M365 is a start, but it’s not a full inventory. True compliance automation must account for every environment: RMM data, vulnerability scanners, remote endpoints, BYOD, shadow IT, even IoT.
Most MSPs struggle to define what an “asset” really is, and if you can’t define it, you can’t govern it. The goal of any compliance automation tool should be to unify that data, but more importantly, to attach ownership, review cycles, and policy linkage. That’s governance in action and that’s what auditors look for.
When Automation Creates a False Sense of Security
The 2024 City of Hamilton, Ontario ransomware breach is a painful reminder of what happens when automation replaces accountability.
On paper, the city appeared compliant. Automation confirmed that MFA was “enabled.” In practice, MFA was only applied to administrative accounts, not to the rest of the organization. When attackers exploited those gaps, the city faced more than $18 million in damages, 80% of systems offline, and a denied cyber-insurance claim.
Automation confirmed settings, not safeguards, and that distinction cost millions.
Automation Can Collect Data, Governance Proves Compliance
At Compliance Scorecard, we approach automation differently.
Our platform can help with the data collection and mapping process across multiple sources; RMM tools, Microsoft 365, vulnerability scanners, and other SaaS platforms, and ties each sync to a governance workflow built on the 4A model:
- Alignment
- Authorization
- Assessment
- Adoption
That 4-part governance process creates a verifiable audit trail. Every action links back to a specific control, policy, and responsible owner. The result isn’t just faster compliance work, it’s provable compliance.
This approach bridges the gap between automation and accountability, what we call GRC Engineering. It ensures that every automated process is supported by governance, ownership, and evidence, making audit readiness a byproduct of daily operations.
CIS Controls: How Far Can Microsoft 365 Automation Go?
Many MSPs begin their compliance journey with the CIS Controls because they provide a practical foundation for small and mid-sized businesses. We did the same, starting with CIS Implementation Group 1 and aligning directly with the Microsoft Graph API to measure how far automation could actually take us.
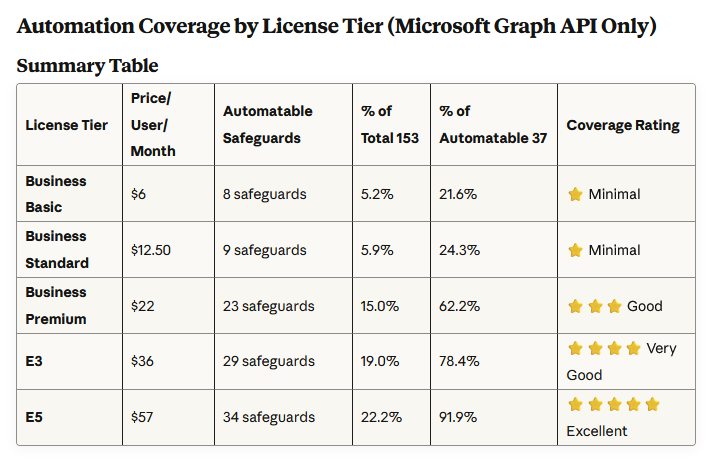
Our findings lined up with the data: even the best automation only goes so far. Out of 153 total CIS safeguards, only 37 can be automated through Microsoft Graph, about 24% overall coverage. With Microsoft 365 Business Premium, that equates to roughly 15% automation, or about two to three safeguards per control. Stepping up to E3 raises coverage to around 19%, and E5 tops out near 22%.
When combined with third-party tools like RMM and vulnerability scanners, total automation potential reaches 50–70%, still leaving about 30% of controls manual by design. Those remaining areas (documentation, policy validation, and evidence review) require human verification no matter how advanced the stack.
Key Findings from Microsoft 365 Automation Testing
- Only 24% of CIS safeguards are automatable through Microsoft Graph API.
- Microsoft 365 Business Premium covers roughly 15% of total safeguards; E5 plans reach about 22%.
- Even with third-party integrations, full automation potential tops out near 70%, leaving about 30% of safeguards dependent on human governance, policy validation, and documentation.
The takeaway: real compliance strength doesn’t come from automating everything, it comes from understanding what Microsoft 365 can (and can’t) automate, and building governance around the rest.
From Automation to Accountability: The GRC Engineering Approach
Automation without governance is noise. Data without ownership is a risk. Compliance without context is chaos.
Compliance isn’t just about collecting information; it’s about connecting it; linking technical data to human oversight. That’s the difference between compliance management and governance, risk, and compliance (GRC) maturity.
We built Compliance Scorecard to make that connection visible. Our goal isn’t to automate compliance for the sake of convenience, but to make compliance repeatable, verifiable, and aligned with how MSPs actually operate.
That’s what we mean by GRC Engineering: transforming automation into assurance, and data into trust.
Final Word
Anyone can build a tool that pulls configuration data. Only a few can engineer the governance systems that turn that data into proof.
Compliance automation isn’t about replacing people; it’s about empowering them. The strongest MSPs use automation to support governance, not skip it. Because at the end of the day, compliance automation only works when governance leads.
Automation gives you visibility. Governance gives you defensibility.
If you’re ready to move beyond check-the-box automation and into measurable, defensible compliance, that’s the work we’re here to do with you.