Strategic Partner | ConnectSecure
Deliver your clients from cyber risk.
Purpose-built by MSPs for MSPs, the ConnectSecure Cybersecurity Platform empowers you to harden the attack surface of your clients amid rising cyber threats and compliance pressures. With a multi-tenant view and all-in-one design, it features everything you need to profitably ramp up your cybersecurity practice with ease.
Target vulnerabilities and become the partner every business needs
Here’s a message for your clients: Prevention is more affordable than going to war. ConnectSecure enables you to put that argument to practice, identifying, prioritizing, remediating, and reporting on security gaps across networks and private-hosted applications, IoT, cloud applications, and more. By introducing an easy and risk-free way to prevent exploitation, your clients won’t be the only winners.
Focus on the pre-event side of the NIST Cyber Defense Matrix
The first two functions of the matrix—Identify and Protect—both serve to minimize vulnerabilities, unlike Detect, Respond, and Recover which define what the response to an attack looks like once it occurs. The ConnectSecure platform focuses on Identify and Protect— reducing the number of episodes that require activation of the next three steps.
Leverage continuous assessments. Wow with in-depth reports. Enjoy revenue growth.
ConnectSecure helps you broach the crucial topic of proactive cybersecurity and deliver value from the outset:
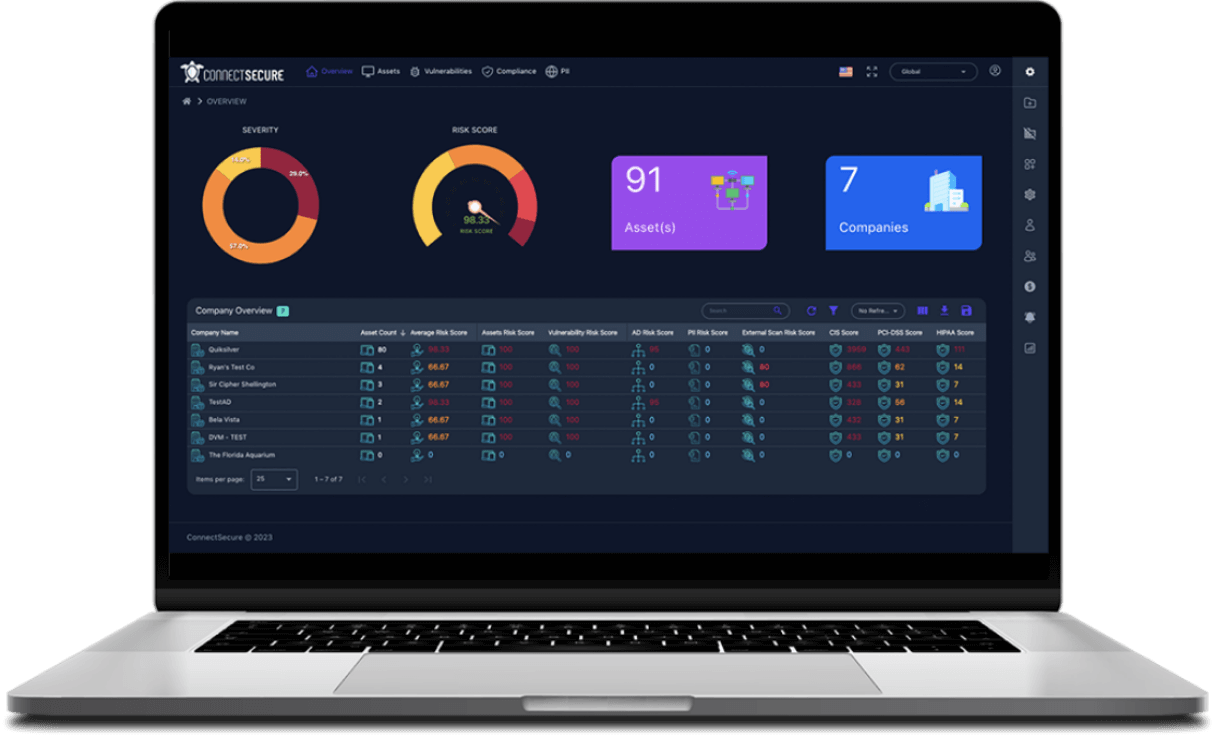
Uncover everything with a vulnerability assessment (agent-based or probe/lightweight) and ensure adherence to key standards and regulations, such as CIS, GDPR, HIPAA, NIST 800-171, NIST 800-53, PCI DSS, and more.
Generate in-depth, white-labeled reports, conveying your clients’ Consolidated Risk Score as well as scores for all assessment areas, and so much more.
Build recurring revenue with continuous external and domain-level scans, featuring near real-time mitigation of new vulnerabilities and prioritization of critical threats as a result of our integration with the National Vulnerability Database (NVD) and the Exploit Prediction Scoring System (EPSS).
Why use several tools when you can have it all in one?
- Asset Discovery
Discover all IP-based assets on your clients’ network(s), providing not just visibility, but in-depth insights for informed decision-making. - Vulnerability Management
Proactively identify and address security weaknesses with automated continuous scanning and remediation across all operating systems, and enjoy support for over 600 third-party applications, prioritization of vulnerability remediation efforts, and more. - Patch Management
Minimize the risk of security breaches with automated third-party application patching, Microsoft operating system patch checks, advanced patch customization, patching schedules, and cross-platform support. Compliance Management Ensure adherence to key frameworks (CIS, GDPR, HIPAA, NIST 800-171, NIST 800-53, and PCI DSS, etc.), covering both technical (registry keys, scans, software information) and contextual aspects (policies, procedures, physical security) - Compliance Management
Ensure adherence to key frameworks (CIS, GDPR, HIPAA, NIST 800-171, NIST 800-53, and PCI DSS, etc.), covering both technical (registry keys, scans, software information) and contextual aspects (policies, procedures, physical security) - Personal Identifiable
Information (PII) Scanning Leverage wide-ranging, automated coverage at both global and company levels to ensure protection of PII data. - Attack Surface Scanning
Gain complete visibility with Deep Attack Surface Scans at the domain level and receive threat intelligence on open ports, target IPs, DNS records, subdomains, emails/usernames, and more. - Active Directory Auditing
Use on-site and Microsoft Entra ID scanning for MFA, provide Office 365 Risk Scoring, discover Azure assets and manage licences, get anomaly alerts sent to integrations, and receive information on user accounts, group policies, and more. - Reporting
(Custom, Standard, White-Label) Drag and drop to provide well-designed, role-specific reports with white-label options in MS Office formats for technical and management reviews. - Active Threat Management
Provide enhanced protection with EPSS (Exploit Prediction Scoring System) to better prioritize vulnerability remediation efforts.